Chez Topsec Cloud Solutions, nous sommes des pionniers de la sécurité du courriel et du web basée sur le cloud depuis plus de vingt ans.
Notre parcours a commencé en 2002. Depuis, nous sommes devenus une force de premier plan dans la fourniture de services de sécurité gérés de premier ordre.
Avantages de travailler avec des solutions Topsec Cloud :

Planifiez une consultation gratuite
Have An Additional Layer of Security That Sits Within O365 For Your Internal Emails.
Home » Our Services » Inbox Protect
Topsec Inbox Protect provides advanced security and protection across internal mail.
Our latest service offers a quick and easy setup to add internal inbox scanning directly into user mailbox accounts, removing threats and preventing interaction with potentially malicious mail.
Our Inbox Protect helps Microsoft users to scan and replicate the gateway within their mailboxes. Microsoft will notify Topsec Inbox Protect of any new internal mail, and Protect will query the mailbox, retrieve it, and process it through our security scanners. Any mail that fails our scanning process will be removed from the user’s view and quarantined locally.















Even though O365 has its protection methods for users, it is still possible for certain spam and phishing emails to get through. Evolving tactics, zero-day attacks, polymorphic threats, targeted attacks, and user errors can occur anytime. These can lead to certain spam and phishing emails; in this case, O365 cannot be foolproof.
Phishing attacks are a potential threat to email security as many cyber criminals use different methods to trick you through email to steal your valuable information.
Hackers use malware and ransomware to gain unauthorised access, which increases the risk of losing valuable data, and even disrupts the system services. They can be a threat to email security.
Cybercriminals/hackers use business email compromise (a phishing attack) to send unwanted emails to different organisations to steal money and critical information.
You might not be aware of who is sending you spam and unwanted email with a motive. It could expose your critical information and cause data loss.
Data breaches and unauthorised access can give access to unknown persons, leading to the loss of critical and confidential information.

Having inbox protection and O365 helps you build a second-layer approach, ensuring advanced threat protection and data and email fraud prevention.
Internal protection scans your incoming and outgoing mail, strengthening your internal/external security.
Our inbox protection has an easy setup process. You won't have to worry much. Just follow a few steps, and you are good to go.
Our inbox protection helps you reach your historical mail in around 2 weeks. Get started now!




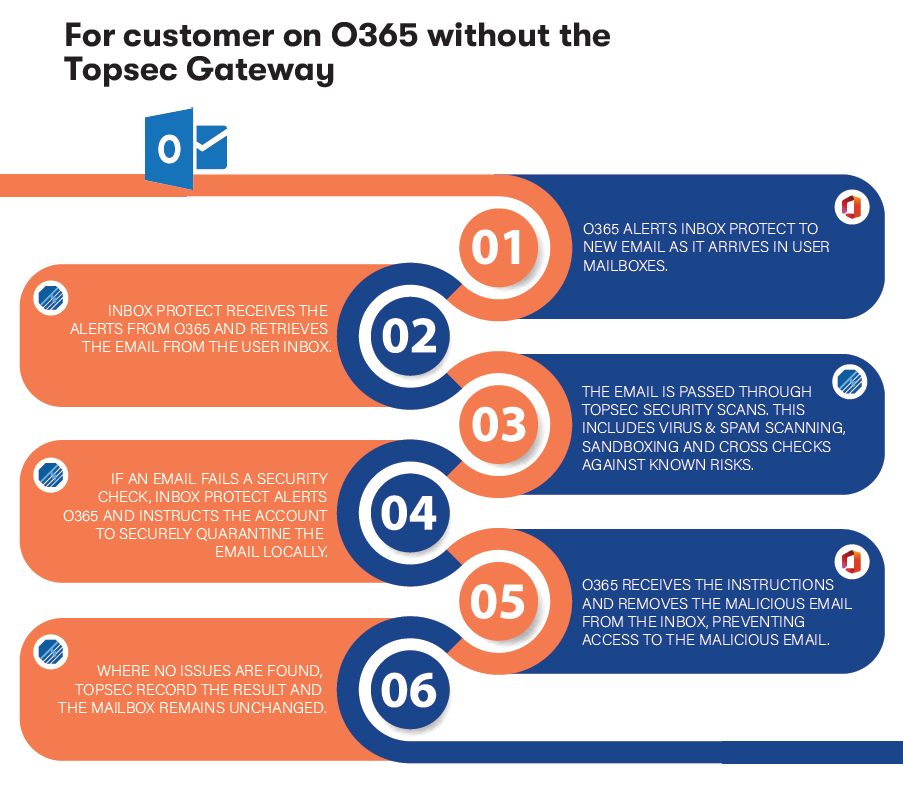
The security service for Office 365 users without a Topsec Gateway provides a multi-step approach to protect against email threats. When new emails arrive, Office 365 sends alerts, prompting Inbox Protect to retrieve and pass them through Topsec’s comprehensive security checks. These include virus and spam scanning, sandboxing, and cross-checking against known threats. If a security risk is detected, Inbox Protect directs Office 365 to quarantine the email, removing any malicious content from the user’s inbox. If no risks are found, the mailbox remains unchanged. This layered security process ensures a safer email environment by proactively handling and eliminating threats.

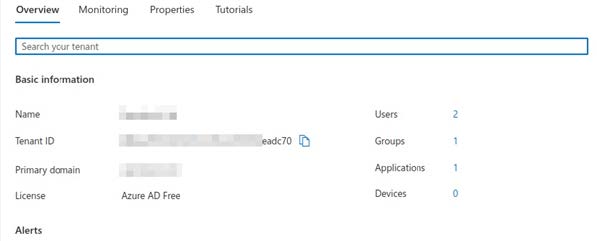
You will first need to obtain your Active Directory 'Tenant ID' from your Microsoft account; this can be found in the Microsoft 'Overview' tab.
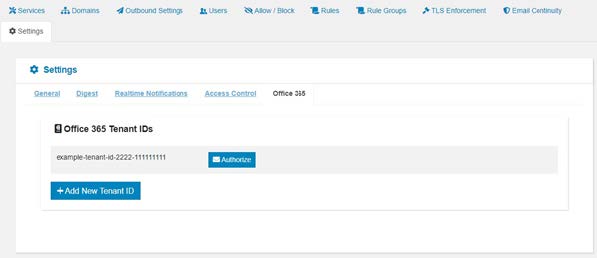
The tenant ID will need to be mailed to our support team (support@topsec.com). Once received we add the tenant to your portal account. With the tenant now added, you will be able to view the setup in the 'Setting/Office 365' tab of your portal account:
To provide permission to 'Topsec Inbox Protect', you will need to authorise the tenant setup by clicking the 'authorise' button. This will prompt a Microsoft login where permissions can be granted:
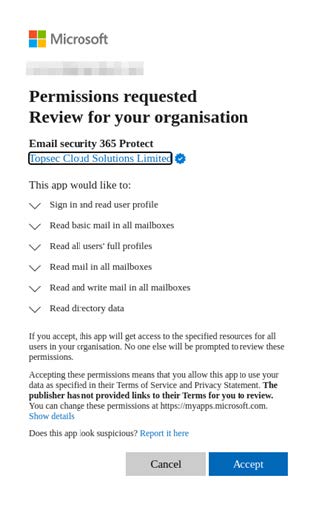
Once acceppted, 'Topsec Inbox Protect' will be activated and functioning.
Topsec uses cutting-edge technology to detect and block sophisticated threats, including zero-day attacks and advanced phishing schemes, ensuring comprehensive protection.
Unique to Topsec, this service specifically guards against impersonation of high-level executives, protecting organizations from fraud and unauthorized actions.
Topsec offers customizable security solutions that cater to the specific needs of different industries, including finance, healthcare, education, and government, providing targeted protection.
With a strong presence in Ireland and the UK, Topsec offers localized expertise and responsive customer support, ensuring that clients receive tailored assistance and guidance when needed.
Topsec’s solutions are designed to help businesses comply with industry regulations, such as GDPR and HIPAA, with features like detailed reporting and audit trails.




Topsec Inbox protection provides a quick and easy setup to add an internal inbox for O365 users, which scans directly into user mailbox accounts, removing any threats and preventing interaction with potentially malicious mail.
Inbox protection assists in mitigating threats like phishing attacks, malware and ransomware, business email compromise, spam, and unwanted email.
Yes, it protects several built-in security capabilities like Machine Learning and AI, Behavioral Analysis, Link and Attachment Scanning, Anti-Spam and Anti-Malware Filters, etc.
By authorising a Microsoft Tenant to allow Topsec Inbox Protect to connect, our gateway scanning replicates within user mailboxes. Microsoft will notify Topsec Inbox Protect of any new internal mail. Protect will query the mailbox, retrieve it, and process it through our security scanners. Any mail that fails our scanning process will be removed from the user’s view and quarantined locally.
Yes, Topsec’s managed inbox protection helps with compliance requirements by protecting users’ sensitive, confidential information and safety.
