Chez Topsec Cloud Solutions, nous sommes des pionniers de la sécurité du courriel et du web basée sur le cloud depuis plus de vingt ans.
Notre parcours a commencé en 2002. Depuis, nous sommes devenus une force de premier plan dans la fourniture de services de sécurité gérés de premier ordre.
Avantages de travailler avec des solutions Topsec Cloud :

Planifiez une consultation gratuite
Guard Your Inbox, Guard Your Peace – Rapid Defense Against Impersonation Scams.
Home » Our Services » VIP Impersonation Protection
VIP Impersonation Protection detects social engineering-based email attacks and stamps an email if triggered. Detecting and stopping these types of attacks necessitates a thorough examination of an email’s content while maintaining delivery speed.
Malicious senders have done their homework. They know the authorised person in an organisation. They usually target staff in the organisation who use names of senior executives or other key personnel.
These attacks rely solely on the name of the person being impersonated and thus usually escape rules designed to capture domain or email address spoofing. These attacks impersonate with a fake name, and bypass firewalls to capture domain or email addresses.
The attacks work by fooling the recipient into believing they have received an internal email from a senior colleague and causing them to take unauthorised actions (such as bank transfers, changes of contact information etc…) based on their instructions.
















We enforce strict email authentication protocols, such as SPF, DKIM, and DMARC, to verify the legitimacy of incoming emails and detect forged or spoofed messages.
Our system assesses the reputation of sender domains and flags emails from suspicious or blacklisted sources for further scrutiny.
VIP Impersonation Protection examines URLs within emails, checking for malicious links and preventing users from accessing potentially harmful websites.
Advanced email filtering techniques that verify the authenticity of incoming messages and validate the sender's identity, preventing email spoofing and impersonation attempts.




Our sophisticated algorithms and machine learning technology analyse email headers, content, and sender behaviour to detect and block impersonation attempts.
We provide real-time scanning and incoming emails analysis, ensuring immediate protection against evolving impersonation techniques.
VIP Impersonation Protection identifies and blocks phishing attempts that exploit human vulnerabilities, protecting your employees from falling victim to scams.
By detecting and blocking emails that impersonate your organisation’s domain, we prevent fraudsters from tarnishing your brand and deceiving your customers.
Our solution helps prevent sensitive information from being leaked or compromised through unauthorised email communications.
If our system detects any social engineering malicious mail, a stamp is immediately sent on the email.

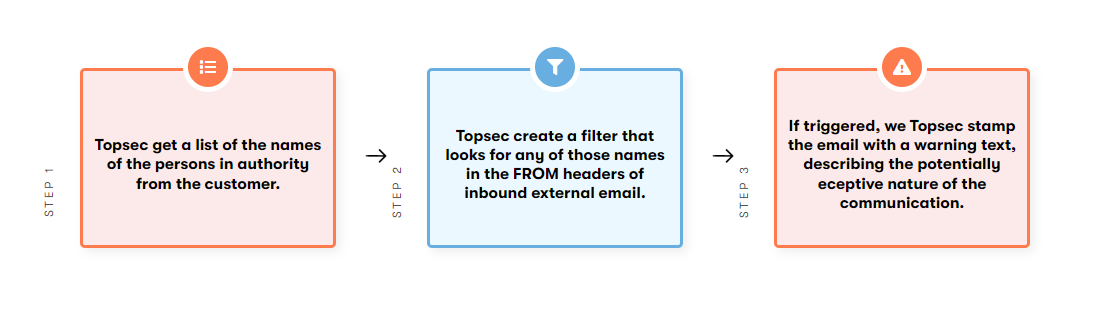
The VIP Rule warns end users in organisations if they get an email from an external source that has a predefined display name of a person in authority that can request delicate information or authorise or request bank transfers or details. To create the rule we would need a list of VIP full names only, no email addresses are required
VIP Display name spoofing. The criteria is we get the Full Name of persons in authority from the customers we add those and variations of those to a text censor.
It will only trigger a warning if they come in from an external source.
The VIP Spoofing rule, matches human names in the display address of an email, against an internal list of senior executives. For example, we see targeted phishing emails that would have a sender address like
“First Name, Second Name” <random1234@gmail.com>
or
“Second Name, First Name” <random1234@gmail.com>
In this case if we “First Name, Second Name” on our list, we would stamp this email with a warning explaining that the email is potentially deceptive, as it is using a Colleague’s name but was not an internal email. The rule only stamps because false positives will occur from time to time.
The rule does not quarantine email. It only stamps it. It is solely based on the human name matching a list of known personnel in the organization.
We have a deep understanding of email security and the evolving tactics employed by cybercriminals.
VIP Impersonation Protection targets impersonation attacks, protecting your organisation from known and emerging threats.
Our commitment to excellence has earned us Recognition and accolades within the cybersecurity industry.
We have a diverse customer base, including organisations in Government, Healthcare, Engineering, Information Technology, and other industries.
Processus de soutien et de gestion d’incidents rapides et réactifs.
We manage your entire email solution, including attachment sandboxing, so you can focus on your business needs.




VIP Impersonation Protection is a specialised email security solution to detect and block email impersonation attempts. It protects your organisation from social engineering-based attacks where attackers try to deceive recipients by impersonating trusted senders.
Email impersonation attacks have become increasingly sophisticated and pose significant risks to organisations. VIP Impersonation Protection provides a proactive defence against these attacks, helping to safeguard your reputation, protect sensitive data, and minimise the financial impact of successful impersonation attempts.
Email is a primary communication channel for any organisation. VIP Impersonation Protection is essential for organisations of all sizes. It adds an extra layer of security to your existing email infrastructure, reducing the likelihood of falling victim to impersonation attacks.
You should consider implementing VIP Impersonation Protection if your organisation deals with sensitive data, has a strong online presence, or is frequently targeted by phishing attempts. It is especially critical if your employees regularly engage in financial transactions, handle confidential information, or interact with external parties.
VIP Impersonation Protection is designed to detect and block various impersonation attempts, including CEO fraud, supplier fraud, business email compromise (BEC), and other social engineering-based attacks that exploit trust and authority.
Yes, VIP Impersonation Protection is user-friendly and straightforward. Our team will guide you through the onboarding process and provide ongoing support to ensure the solution integrates seamlessly with your existing email infrastructure.
