Phishing Attacks in Different Industries: A Comprehensive Overview

Phishing attacks have become a widespread cybersecurity threat, affecting organisations across all industries. These attacks involve tricking individuals into revealing sensitive information, often through deceptive emails or websites.
The Evolution of Phishing Awareness Training

Phishing awareness training has evolved as hacking and phishing have grown in complexity.
Vishing (Voice Phishing): The Growing Threat and How to Protect Yourself

Learn about vishing, a type of voice phishing scam where fraudsters use phone calls to steal personal information. Discover how to protect yourself from vishing scams and stay informed with the latest cybersecurity tips to prevent fraud.
The Anatomy of a Phishing Email: How to Spot Red Flags and Stay Safe

To protect your organisation from ransomware and phishing attacks, it is important to know the anatomy of a phishing email. Read our blog to know more!
Safeguarding Against Quishing: Strategies for Enhanced Cybersecurity
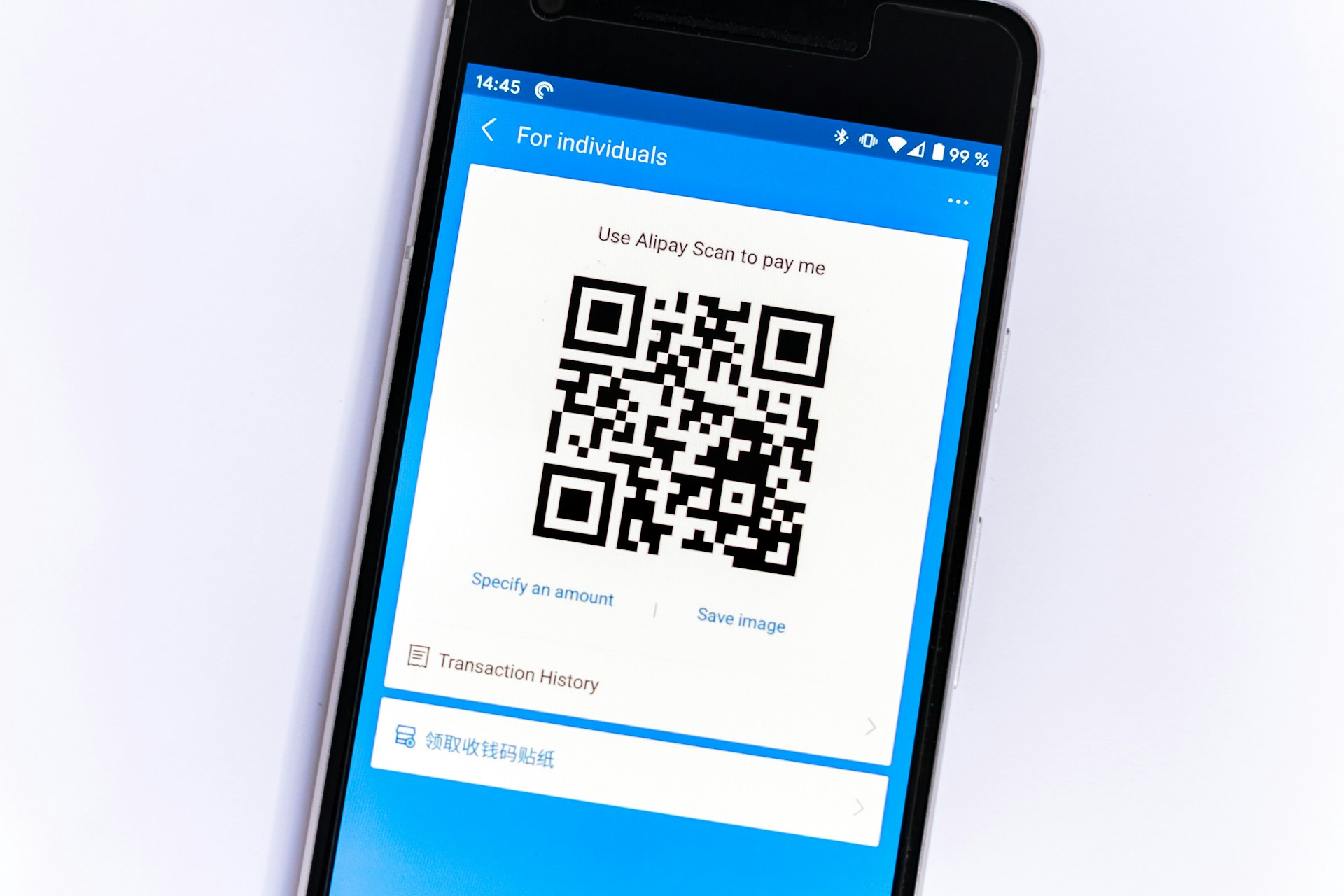
Explore effective strategies to secure your business from QR code phishing attacks, strengthen email security and implement robust cybersecurity measures.
What is Phishing? A Complete Guide

What is Phishing? A Complete Guide Train your employees to watch out and repport phishing emails. Get a Quote Download Datasheet Email Security What is Phishing? A Complete Guide Phishing is a type of online fraud where attackers use social engineering tactics to trick individuals into sharing sensitive information such as passwords, credit card numbers, or other personal data. Read our blog to best know how to protect yourself from these phishing attacks. By Cian Fitzpatrick | April 13, 2023 Phishing refers to a cybercrime where individuals are contacted through email, phone, or text by individuals posing as credible institutions. The aim is to coax them into sharing sensitive data such as personal information, bank account and credit card details, and passwords. This information is then used to access crucial accounts, potentially causing financial harm and identity theft. Phishing Definition To deceive the victim into clicking on a malicious link, phishing employs impersonating a trustworthy source through email, instant messages, or text messages. This can lead to installing malware, system freezing by a ransomware attack, or revealing confidential data. In addition, cybercriminals use phishing as a means to infiltrate corporate or governmental networks, often as part of a more extensive attack like an advanced persistent threat (APT) event. Hackers override security measures, introduce malware, and acquire privileged access to confidential data by compromising employees. A phishing attack can have severe consequences, including unauthorised purchases, theft of funds, and identity theft. If an organisation is targeted, it can result in significant financial losses, damage to reputation and consumer trust, and a decline in market share. Depending on the extent of the attack, a phishing attempt can escalate into a security incident that can be challenging for a business to recover from. How does Phishing work? Attackers send malicious email messages or other communication methods that resemble legitimate ones. The more the message appears real, the greater the chance of success. The attackers’ goals are usually to obtain personal information or credentials, creating a sense of urgency in the message to make users feel threatened. This manipulative technique leads to the victim’s compliance even to unreasonable demands. Organisations must train staff to recognise the latest phishing tactics; it only takes one person to fall for a phishing attempt and trigger a severe data breach. It is why phishing is considered one of the most challenging and critical threats to mitigate. Dangers of Phishing Personal phishing risks Personal phishing targets individuals through phone calls, emails, or text messages. Attackers pose as trustworthy entities like government agencies, banks, or famous companies to obtain sensitive information like credit card details, usernames, and passwords. This information can be used to steal money or commit identity theft. Personal phishing attacks can devastate individuals as they lack the same level of security as large organisations. Individuals should be cautious of unsolicited messages and regularly update their passwords to protect themselves. Organisational phishing risks Organisational phishing is a cyber attack that targets businesses, governments, and institutions using fake emails, text messages, or phone calls to obtain sensitive information such as login credentials, financial data, or other confidential details. Attackers use this data to steal funds or launch advanced attacks. Phishing attacks can result in severe financial and reputational damage, particularly when involving sensitive data or intellectual property. Organisations must implement robust security measures, including employee training, to reduce the risk of falling prey to these attacks. Common Traits of Phishing Phishing is an illegal technique used to trick individuals into revealing sensitive information. Here are some common indicators of a phishing attempt that you should be aware of to stay safe: Requests for sensitive information Generic greetings or lack of personalisation Spelling or grammatical errors Unofficial or unfamiliar sender information Urgent requests or sense of urgency Unfamiliar or mismatched URLs Suspicious or misleading hyperlinks Threats or scare tactics Requests for immediate action Tempting or too-good-to-be-true offers Protect your business from phishing attacks today by signing up for our Managed Phishing Awareness Training program. Click Here Phishing Attacks: Statistics and Examples The 2022 Cost of Data Breach Report by IBM affirms that data breaches are mostly due to the usage of stolen or compromised credentials. Such credentials were the primary attack method in 19% of breaches this year, a slight decline from 20% in 2021. In 2022, 19% of data breaches were primarily caused by stolen or compromised credentials, showing a small decline from 2021’s 20% statistic. The average cost of breaches resulting from this type of attack was $4.5m, and it took 243 days to detect and 84 days to control, which is 16.6% longer than the average time to identify and manage a data breach. Phishing was the second most frequent cause of data breaches, accounting for 16% of incidents and costing $4.91m. Examples: In August 2022, Acorn Financial Services suffered a security breach when an employee was targeted in a phishing attack. The attackers stole login credentials and accessed sensitive information, including client details. Acorn conducted an investigation and informed affected customers. The breach could have been prevented or minimised with a phishing detection system in place. Twilio experienced a security breach in August 2022. The breach was caused by an SMS phishing attack in which employees were directed to a fake authentication site that looked like Twilio’s real site. The employees unknowingly entered their login credentials on the fake site, which allowed the attackers to gain access to Twilio’s internal resources and customer data. The attackers compromised 93 Authy accounts and potentially exposed 1,900 accounts on the encrypted communication app Signal, but they wouldn’t have been able to access message history or contact lists. Types of Phishing Attacks 1) Spear phishing Spear phishing involves targeting specific individuals in an organisation, typically those with high-level access, through email. This tactic aims to deceive victims into providing confidential information, transferring funds, or downloading malicious software. 2) Business email compromise (BEC) Business email compromise (BEC) involves the perpetrator pretending to be someone the recipient trusts, such as
What is Email Security? A Complete Guide

What is Email Security? A Complete Guide Why do you need to have a managed email security solution? Get a Quote Download Datasheet Email Security What is Email Security? A Complete Guide In today’s threat landscape, learning how to protect yourself and your business from cybersecurity and email security threats is essential. This guide will tell you all you need to know about email security and how to prevent malware, spam, and phishing attacks. By Cian Fitzpatrick | March 10, 2023 Email security protects accounts and messages from unauthorised access, data loss, or compromise. To strengthen security, organisations can use policies and tools to prevent threats like malware, spam, and phishing attacks. Email accounts are often targeted by cyber attackers since they provide a vulnerable entry point to other accounts and devices. A single unintentional click can trigger a security breach with severe consequences for the entire organisation. How secure is email? An email was created to promote openness and accessibility, allowing individuals and people from the same or other organisations to communicate with one another. Nevertheless, the inherent security of Email is not dependable, which will enable attackers to bypass it and make money. These attackers conduct spam campaigns, deploy malware and phishing attacks, execute advanced targeted attacks, or conduct business email compromise (BEC) schemes. Due to the extensive usage of Email as a primary mode of communication in most organisations, attackers exploit its vulnerabilities to steal sensitive information. As Email is an open format, it is open to interception by anyone, raising concerns about email security. The issue became particularly acute as organisations began transmitting confidential or sensitive information through email. This could be easily read by an attacker who intercepts it. Organisations are enhancing security measures to deter attackers from accessing sensitive or confidential information. Topsec is also a part of this intense security drive. We offer tailored email security services individually designed for your company’s specialized needs and desires. Types of email threats Data exfiltration Data exfiltration refers to unauthorised data extraction from an organisation, either utilizing manual transfer or malicious software. Email gateways are useful in preventing businesses from transmitting sensitive data without proper authorisation, preventing a costly data breach. Malware Malware is a term for malicious software designed to cause damage or disturbance to computer systems. These malicious software comes in various forms, such as viruses, worms, ransomware, and spyware. Spam Spam refers to unsolicited messages sent in large quantities without the recipient’s consent. Businesses often use spam email for commercial purposes. But scammers use it to spread malware, deceive recipients into sharing sensitive information, or demand money through extortion. Impersonation Impersonation is a deceptive tactic used by cybercriminals who pose as a trusted individual, sender, or entity via email to extract money or data. A business email compromise is one such instance where a scammer acts like an employee with the intent to steal from the company, its customers, or its partners. Phishing Phishing is a fraudulent practice that involves impersonating a trustworthy individual or organisation to deceive victims into sharing valuable information, such as login credentials or other forms of sensitive data. It can take various forms, including spear phishing, smishing, vishing, and whaling. Spoofing Email spoofing is a risky threat that involves tricking the recipient into believing that the Email originates from someone other than the actual sender, making it a useful tool for business email compromise (BEC). Since the email system only reads metadata that the attacker can easily alter, it is difficult for the email platform to differentiate between a fake and a real email. Furthermore, it makes it relatively easy for the attacker to impersonate a person known or respected by the victim. Protect your emails from spam, phishing & malware attacks with Topsec’s managed email security solution. Request A Quote Now & Safeguard Your Business Today! Click Here Why is Email Security Important? For over twenty years, email has been a crucial communication tool in the workplace. With an average of 120 emails received daily by employees worldwide and over 333 billion emails sent and received daily by individuals. However, cybercriminals view the widespread use of email as an opportunity to initiate attacks, such as phishing campaigns, malware, and business email compromise. Shockingly, 94% of all cyberattacks commence with a malicious email. According to the FBI’s Internet Crime Complaint Center (IC3), cybercrime caused over $4.1 billion in losses in 2020, with business email compromise causing the most significant harm. The impact of a successful attack can be severe, leading to significant financial, data, and reputational damage for organisations. Therefore, email security is necessary to prevent unauthorized access to sensitive information, to ensure business continuity, and to uphold trust with customers and stakeholders. Email Security Policies In today’s corporate world, email has become an indispensable tool for communication, leading many organisations to implement protocols for handling email traffic. One of the initial policies that most businesses adopt pertains to monitoring the content of emails passing through their email servers. Determining the appropriate actions based on the email’s contents is critical. Once the fundamental policies are in place, companies can implement additional security measures to safeguard their emails. Organisations can implement various email security policies, ranging from basic measures like filtering out executable content to more complex ones, such as subjecting questionable content to in-depth analysis using sandboxing tools. For security incidents, the organisation must clearly understand the nature and extent of the attack to assess the damage caused. By having visibility into all outgoing emails, organisations can also impose email encryption policies to ensure that sensitive information is not compromised. Email Security best practices To establish good email security practices, organisations should consider implementing a secure email gateway as a first step. This gateway is responsible for scanning and filtering all inbound and outbound emails to prevent malicious threats from entering the system. That said, traditional security measures like blocking suspicious attachments are no longer adequate due to the increasing sophistication of cyberattacks. Hence, organisations should deploy

