At Topsec Cloud Solutions, we’ve been pioneering cloud-based email and web security for more than two decades.
Our journey began in 2002. Since then, we’ve become a leading force in providing top-tier managed security services.
Benefits of working with Topsec Cloud solutions:

Schedule a Free Consultation
Detect, Defend, Secure – Empower Your Cyber Defence with Breach Detect.
Home » Our Services » Breach Detect
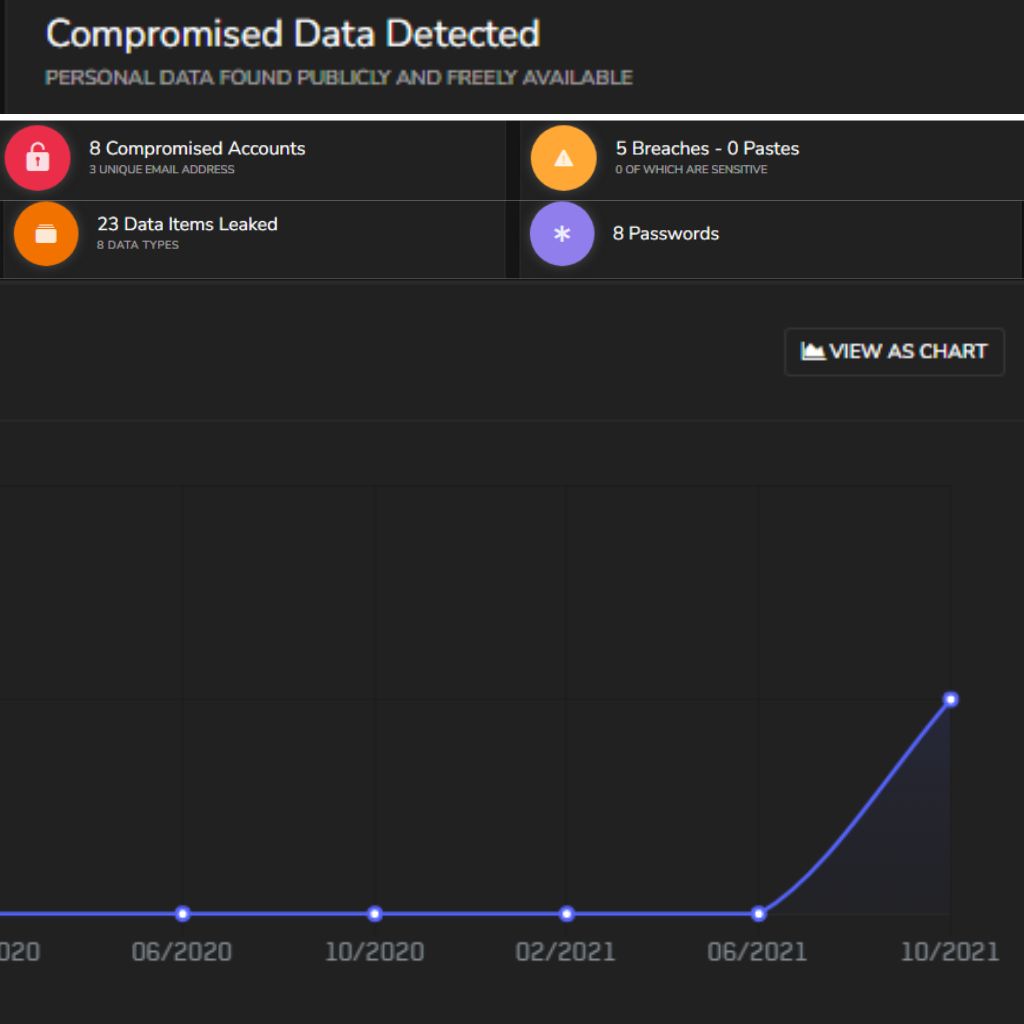
Topsec Breach Detect continuously finds, analyses, and monitors compromised credentials on the Dark web.
Topsec Breach Detect is an automated technology that proactively monitors the Dark Web to look out for any leaked or compromised login credentials from both public and private security breaches. In the event that any of your data has been breached and made available online on the Dark Web, Topsec immediately detects it and notifies you to take prompt action.
Cybercriminals find a way to get into your computer system and steal your invaluable personal information. For example, names, credit card numbers, email addresses, usernames, passwords, behavioural data, biometric data, etc. are stolen from your computer and often sold on the Dark Web.
The extent of the damage could very well exceed estimates. Your entire business becomes vulnerable to more disastrous forms of phishing and ransomware attacks. Since your highly sensitive data is easily available on the Dark Web, any other ill-intentioned individuals can also use it against you.
At Topsec, we believe in ensuring your safety and that of your organisation by taking prompt and necessary actions to implement recommended measures and corrective actions against data breaches.




















We instill a safer staff culture where your employees will understand the correct way to use passwords and acknowledge why managing data breaches is important.
We provide our clients with breach notifications carefully evaluated to improve and remediate password malpractices.
Topsec will immediately provide notifications if we find any of your credentials in any data breaches online.
Topsec ensures the organisation and supply chain are in accordance and compliant with your privacy standard.
Breach detect services automates the process of monitoring and analyzing vast amounts of network data, saving valuable time and resources for organizations.
Through machine learning and behavioral analysis, Breach Detect can quickly identify patterns and anomalies associated with potential breaches.

With the Breach Detect service, we generally deal with sensitive information, which requires a nominated email address (DPO,CISO) to be provided for notifications and intimations once and if there is a breach.
An aproval mail is then sent out from our sysytem to the nominated email address for confirmation. Once the nominated person confirms and authorises access, Topsec Breach is now in use.
Once the service is in place, our representative would then have an introductory review call to go through all the raw data available on the dark web for your organisation.
During this call, after analysing the data, the representative might suggest remediations, training on password management and how to protect your internal passwords from third party apps. Notifications are always sent in Real-Time if and when a breach occurs on the Dark Web.
As a leading email security provider, Topsec possesses deep knowledge and experience in email security best practices.
Topsec manages your entire email solution for you so you can focus on your business needs.
Tailored solutions based on specific business needs and requirements.
Successful deployments and customer references in diverse industries and use cases.
Fast and responsive support and incident/threat management processes.
Topsec is always a call away when you are facing any email security issues.




Breach Detect is a premium cybersecurity service by Topsec to provide protection and countermeasures against data breaches. We do so by aggressively looking out on illegal websites for stolen information that has been kept for sale.
Leakage of your highly sensitive information into the wrong hands can lead to severe consequences. Having BreachDetect allows you to be secure from such data breaches and possible cyber security threats as Topsec constantly scan for such violated or stolen data thoroughly on the internet.
Data breaches are becoming more of a common occurrence. Organisations that store valuable and confidential information on their database but have weaker security systems are more prone to fall victim to these cyberattacks. Topsec Breach Detect will keep your data and information protected at all times and allow you to take preventive measures.
Breach Detect can detect sensitive information that are unintentionally exposed through accidental storage in publicly accessible online locations, insecure transfer, or due to errors, negligence, or unauthorised access. Cyberattacks, insider threats, physical theft, and weak access control measures can also lead to data breaches. Topsec takes proactive measures to ensure that these cybercrimes are detected promptly.
Acquiring the services of a top internet security provider will ensure your organisation of robust protection against cyber security breaches. Experts at Topsec ensure the correct installation and configuration of your organisational database, leaving minimal room for hackers to get access. Furthermore, firewalls, anti-virus, and anti-spyware software are also useful in protecting your business from data breaches.
The stolen data in a Data Breach can include various types of personal information, such as bank account details, online passwords, passport and driver’s license numbers, social security numbers, medical records, and online subscriptions.
Healthcare, Government, Non-Profit, Finance and Insurance organisations are most prone to cyberattacks such as data breaches. However, any organisation that holds crucial confidential information and has a weaker security system can fall prey to cyberattacks.
