Home » How to Build a Resilient Email Security Architecture
By Cian Fitzpatrick | 1st May 2024
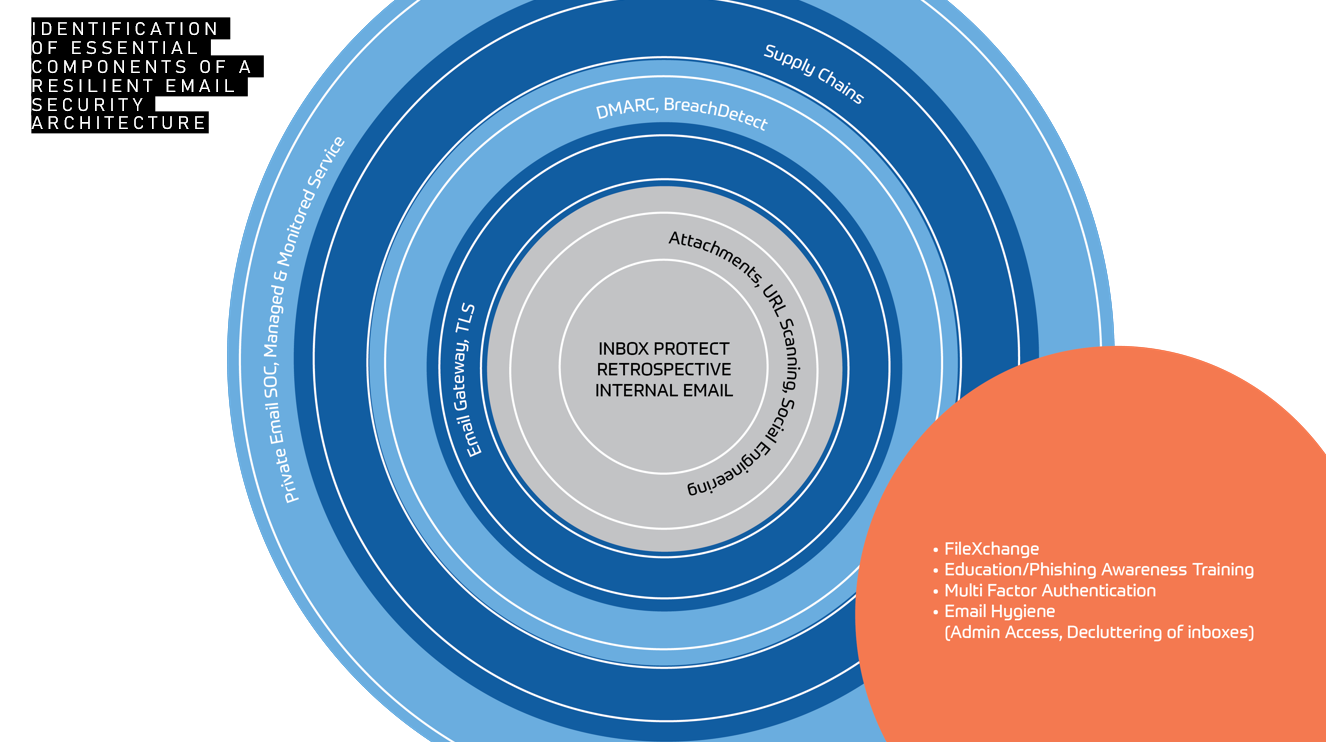
Bad actors are getting smarter. We’re seeing more malicious QR codes within emails and email attachments. They often appear harmless at first, but post-delivery, they’re able to change destination or characteristic. Likewise with URLs, threats can be triggered and clicks redirected, hours or even days after arrival in an inbox. This can make it difficult for gateway security systems to nab threats as they enter a domain.
There’s also been a rise in OneDrive as a delivery method of malicious threats, with files that look initially like they contain nothing untoward. Again, threats are triggered some time later.
Whaling and spear phishing attacks are on the increase, where senior staff is tracked and targeted. Information is accumulated from across the web, using social media, and professional platforms to find out who’s-who and where they are. Impersonation techniques involve the clever use of AI and other easily available technology. Remember that this is an industry the size of a country’s economy (third after the US and China, in fact).
Compromises in the supply chain are also growing. The use of contractors can be risky. But who doesn’t use contractors and partners? If a supplier’s security is not up to scratch, the knock-on can be huge, and cybercriminals are exploiting smaller suppliers to funnel into larger organisations. Partners are often trusted and the relationship is solid, and so systems don’t flag them up.
Human behaviour will always be a stumbling block for organisations. And not just users who are prone to social engineering – which is all of us – there’s also the risk that protocols like DKIM/DMARC are not set up correctly. Compliance regulations and cyber insurance policies may demand these protocols, but correct set-up takes effort and understanding. IT departments are under huge pressure, it’s not surprising then that these protocols become a mere box-ticking exercise. IT staff are often at the point of burn-out and their familiarity with risks, or incessant flags on the systems they monitor, can hinder them from seeing the wood for the trees.
Central to protecting a cyber environment is a proactive approach. Constant staff-awareness training should be one arm of defence, and technology, the other.
A proactive approach means tackling emails before they reach inboxes, before they’re in transit on an organisation’s infrastructure. Once a threat is in an inbox, it could be too late. The onus is then on the user to determine that the email is fraudulent, and this could be the weak link. The sophistication of these scams lies in their appearing sound of character, links and attachments are unthreatening. But they’re manipulable once they’ve reached their destination, and that when they attack.
Scammers are taking less of a birdshot approach now. They’re targeting specific people or roles in an organisation, and starting a process of engagement which begins innocently enough. Like this, their emails seem legitimate and go unflagged. Once they have you on a trusting journey, they’re able to lead you to malicious content.
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication protocol. Its aim is to protect an email domain from unauthorised use, particularly email spoofing, or the creation of forged email addresses. Set up DMARC Protection correctly in order to protect businesses from email-based compromises, phishing scams, and other cyber threat activities.
On entry to an organisation, an email encounters an antivirus scanner, where it will be reviewed for legitimacy. DMARC and DKIM protocols will be correctly configured and vulnerabilities are constantly monitored on the Dark Web. The AV scanner will look at whether an email’s credentials have been previously encountered, if there’s an existing fingerprint for it, whether or not it has an attachment, link, or QR code. There are three options at this point. The email may be found to be legitimate and risk-free, it may be deemed malicious and blocked, or it may go into a sandbox for further investigation. There are several sandbox environments, one for attachments, one for URLs, one for QR codes.
An email sandbox is an isolated environment identical to the user environment. It’s like a laboratory, where an attachment can be exploded or code can be executed in the vacuum of the sandbox without affecting or bringing down the entire network. Sandboxes are particularly effective against Advanced Persistent Threats (APTs), which are custom-developed, targeted attacks. Their aim is to steal data and they’re designed to elude traditional detection methods. Human intervention and observation allows for further research into an attempted attack and action taken. The knowledge and experience of people cannot be underestimated in cybersecurity.
You can have all the best systems in place, solid procedures, cutting edge technology, and the most vigilant IT team, but ultimately, the target for cybercriminals is you and me. Every person in an organisation is a possible access point for a scammer. And so it is up to each person to be the obstacle that halts the threat.
It’s a big ask, but not impossible.
With ongoing education and awareness building programmes, employees will be vigilant and proactive. We’re all fallible, gullible and open to manipulation. And scammers have all the time in the world to come up with scammy strategies, while most of us just want to get on with our day jobs. Everyone needs to be on board and understand the implications of a data theft or system breach.
Cybersecurity staff carry the load and the pressure of an organisation’s technology safety.
Budgets are getting ever-tighter, placing even more weight on these teams. If things go wrong, in which direction will the finger-pointing go? This level of responsibility leads to far-reaching consequences, from health-related issues resulting from stress, mental health problems, and burnout.
Organisations need to use their budgets wisely and efficiently, but this is not the time to bury heads in the sand. Cybercriminals are constantly scanning for opportunities, and every organisation and every person is a potential opportunity. With good systems and policies in place and an ongoing education programme, organisations can – and must – win this battle.
Contact us for help in ensuring your organisation is compliant with DMARC rules. Topsec Cloud Solutions is dedicated to assisting businesses in navigating these changes and ensuring seamless compliance with DMARC standards, thus securing their digital communication channels for the future.
