Vishing (Voice Phishing): The Growing Threat and How to Protect Yourself

Learn about vishing, a type of voice phishing scam where fraudsters use phone calls to steal personal information. Discover how to protect yourself from vishing scams and stay informed with the latest cybersecurity tips to prevent fraud.
Meet the team: Digital Marketing Manager, Rianka Gupte

Topsec’s Senior IT Architect, Alan Buckley shows us why designing with flair is the best way to combine human and machine.
The Anatomy of a Phishing Email: How to Spot Red Flags and Stay Safe

To protect your organisation from ransomware and phishing attacks, it is important to know the anatomy of a phishing email. Read our blog to know more!
Meet the team: Senior I.T Architect, Alan Buckley

Topsec’s Senior IT Architect, Alan Buckley shows us why designing with flair is the best way to combine human and machine.
Email Security: A Priority for Small and Medium Enterprises

Email Security: A priority for Small and Medium Enterprises. Email security is a critical priority for businesses of all sizes Get a Quote Download Datasheet Email Security > Email Security: A Priority for Small and Medium Enterprises By Cian Fitzpatrick | 3rd June 2024 As a small-to-medium business, you might think you don’t need to be concerned with all this cybercrime stuff. Cybercriminals don’t care for small businesses. The takings are too small. This couldn’t be further from the truth. But oddly, it is a widely held misconception. There’s a certain logic here that cybercriminals would be well aware of: big businesses have big budgets, right? They can spend a fortune on protecting their digital assets. Conversely, smaller businesses have smaller budgets, and probably less digital assets to protect (we’re talking data, the new gold). The return might be smaller, but the fruit is hanging lower. While you might think that you’re a small fry and don’t really need security for your business, make no mistake, that someone out there thinks you’re fry enough. And cybercrime is a growing economy, it’s become an easy trade, with ready-made software solutions available on the Dark Web. The facts are not optimistic. Cybercrime is the number one threat when it comes to financial crime in Ireland, says the Compliance Institute, which surveyed 230 compliance professionals working in Irish financial services. Hacking, phishing, online scams and other forms of cybercrime have overtaken tax evasion and insider trading. And anybody who accesses the internet, is a target and possible victim. So while smaller businesses are squeezed for resources, they simply cannot afford to neglect this issue. According to a 2022 report by Grant Thornton, cybercrime was going to cost Ireland more than €10bn that year. That’s a lot of money leaking out of the economy. The same report showed that one in three SMEs fell victim to cybercrime between May ’21 and April ’22, with an average pay-out to fraudsters at €22 773 per incident. But 2023 figures say that nearly three in four businesses (not necessarily SMEs though) had been attacked in the 12 months prior. That same report says that Ireland had the highest median average number of attacks, Ireland is the country most likely to pay a ransom and that the number was four times higher than the previous year. There is a silver lining however: The single biggest attack in Ireland in 2023, cost €118,128, down from €5.2m in 2022. Silicon Republic has also said that according to Hiscox Business Insurance, Ireland has the highest rate of cyber-insurance ownership of all the countries surveyed, which included the UK, Belgium, France, Germany, Spain, the Netherlands and the US. The direct financial implications are obvious, but less obvious is the reputational and trust damage that results from these issues. As well as private data that is now “in the wild”. Protect Your SME with topsec cloud solutions Get A Quote Types of cybercrime that target SMEs: Ransomware, as the name suggests, kidnaps data until money is paid over, simplistically. This is malware that blocks access to a victim’s data by encrypting it, and a decryption key can be “bought”. Business Email Compromise, BEC, attacks specific employees that have access to company funds or sensitive data. This is often combined with impersonation, where a fraudster will pretend to be a senior staff member or client. They’ll request money or access to systems. Password attacks unsurprisingly, involve cybercriminals using a range of methods to learn credentials. One study in 2022 found that more than 80% of successful hacks are as a result of accessing user login details. Social engineering, phishing, brute force, are all methods of gaining the information that’ll get a criminal in, either providing access to sensitive systems and data, or even to money. SMEs are just as much at risk of social engineering attacks. A recent report from 2022 says that organisations with over 2000 employees are only slightly more of a target than their counterparts with less than 100 employees. The number of attacks on a larger enterprise is far more, but as a percentage, it remains more-or-less the same. The bigger issue is that the cost of a breach is generally far more devastating for a small company, than it is for a larger organisation. Cybersecurity Ventures says that 60% of small businesses will close their doors six months after a security breach. This is a huge threat to small businesses, with 43% of online attacks focused on SMEs currently. Of concern should be that SMEs are seemingly unprepared for an attack. A 2023 report found that almost 25% of SMEs had either been attacked or hadn’t realised they’d been attacked in the 12 months prior. 61% of SMEs didn’t have dedicated cybersecurity experts, 47% didn’t have an incident response plan and 27% didn’t have cyber-insurance coverage. What can you do? Every company is experiencing budget cuts right now. It’s tight, but a large part of being a secure company is phishing awareness. Employee training and instilling security consciousness into each and every staff member is key. Regular training on identifying a potential “phishy” email, or social engineering and impersonation attempts are crucial. Multifactor authentication is an account login process that demands more than one method of logging in. It may involve a password as well as a security token, or biometric verification. Software systems that prevent dodgy emails from even entering an organisation’s domain are a favourite preventative measure. If measures can be taken to halt the threat before it even reaches inboxes, that’s ideal. An incident response plan should also be in place. A cyber attack has become a likely event in today’s world, and planning for the eventuality may help limit the damage. It also generates a preventative-approach-mentality. Forewarned is forearmed. More and more, legislation is forcing companies – big and small – to take responsibility for their own environment and accountability for a breach. Organisations are only really holders of data, not owners. The onus is on these companies to
DMARC is now compulsory, thanks to Yahoo and Google.

DMARC is now compulsory, thanks to Google and Yahoo. Email Security requires DMARC Protection. Get a Quote Download Datasheet Email Security > DMARC DMARC is now compulsory, thanks to Google and Yahoo. By Cian Fitzpatrick | 17th May 2024 Not the cool kid in town, and as old as the internet itself, email remains the most productive business tool. By the same token, it’s the most effective tool for cybercriminals. With this in mind, regulators have been focusing on email security in an attempt to curtail cybercrime. As methods became more sophisticated than simply poorly worded emails promising royal riches from secret vaults in places unknown, so too have security protocols and technology to halt the incoming onslaught. Proactive security solutions are the only way to protect organisations in this age where data is gold. DMARC is now a compliance issue Domain-based Message Authentication, Reporting, and Conformance, also known as DMARC, is a solution developed to be highly effective in email security. So much so that Google and Yahoo have implemented stringent DMARC regulations taking effect in February of this year for senders of 5000 or more messages per day. Email domains must have a DMARC policy in the DNS (Domain Name System) and messages must pass DMARC alignment, or they won’t be delivered to Yahoo and Gmail inboxes. This applies to messages sent on an organisation’s behalf through email service providers such as MailChimp. The DNS is the equivalent of the internet’s phonebook – remember those? We access websites through a name, but web browsers talk to each other through IP addresses, so the DNS essentially converts domain names to IP addresses. What’s DMARC? DMARC integrates SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to verify an email’s authenticity. One of the biggest issues in recent security breaches has been that attackers can impersonate a domain, making an email look like it comes from someone, when it really comes from someone else (a fraudster). DMARC is a robust solution that makes sure to check that the email originates where it says it originates, and can then block phishing and impersonation attempts. DMARC relies on two key elements: SPF confirms the origin of an incoming email. And DKIM, which uses encryption to authenticate an email and prevent identity forgery. DMARC records instruct recipient servers on handling emails that fail authentication checks, either by quarantine or outright rejection. This may be flagged due to a difference between a supposed email sender and the actual email address. It’s a crucial layer of defence. In the old days, platforms like Google relied on filters to sieve out spammers and fraudsters. The filters were often so severe that legitimate emails would be blocked. Cyber security is always a fine line between keeping a system safe and minimising user discomfort. Get DMARC Compliant with Topsec today Get A Quote More than just compliance, it’s about trust. Google and Yahoo’s move to compel businesses to adopt DMARC is encouraging. On one hand, organisations are teaching their employees to have a healthy distrust of email. However, as a brand and organisation, you want those with whom you engage to trust your digital communications. By implementing solid security measures like those offered by Topsec Cloud Solutions, it’s an opportunity to strategically raise your brand profile as one that can be trusted. The DMARC initiative by Google and Yahoo isn’t purely about technology. The three pillars behind this strategy from a user’s perspective are that email will be authenticated in the background (as discussed above), it will be easy to unsubscribe from mailing lists, and emails cannot be spammy – they have to be wanted by recipients. This is a positive move for users and organisations, although it does mean that businesses may have to review their technology strategy if they send more than 5000 emails a day. The idea is to encourage and enhance trust in email communications and to proactively protect against fraud. For organisations that have yet to implement DMARC, it’s an opportunity to ensure the protocol is correctly executed, but it’s also as a confidence-building practice within and across organisations. There’s an element of brand reputation and integrity in all of this. Who doesn’t want to do business with an ethical organisation that looks after its assets and its clients’ assets? For marketing teams, it’s a chance to demonstrate outstanding values and a security-aware ethos. This is not just a technology issue. Once again, it’s highlighted that cybersecurity belongs to each stakeholder in the business. There’s also the compliance angle. Failure to comply will lead to delays in email delivery and possible rejection. The effect on brand reputation and trust in integrity will be significant. And that’s the best-case scenario. The possibility of a cyber attack becomes very real for organisations that don’t comply, or which implement DMARC incorrectly. These attacks have devastating financial and reputational consequences. It’s the responsibility of each organisation to secure their digital channels. Recovering from a phishing or spoofing attack is expensive, time-consuming, and incredibly stressful for stakeholders. Data and privacy breaches become a nightmare for everyone and the damage can be permanent, or at best, lengthy to repair. DMARC in practice. Both Google and Yahoo offer transparent error codes for each email rejection. The error codes are freely available and offer an explanation along with the numerical code, making it easy to understand why an email was blocked, and what action should be taken. Failures are generally either temporary or permanent. With 90% of all cyber attacks initiated through phishing, which is generally done via email, it’s understandable that the largest tech organisations are taking control. By forcing companies to protect themselves and their users, they’re helping to make the internet a safer place and combat cybercrime. This is and always will be a process, but organisations need to work together. And this is more than a security issue, it’s a chance to prove to clients that your organisation is taking security seriously. Our DMARC Protection
How to Build a Resilient Email Security Architecture
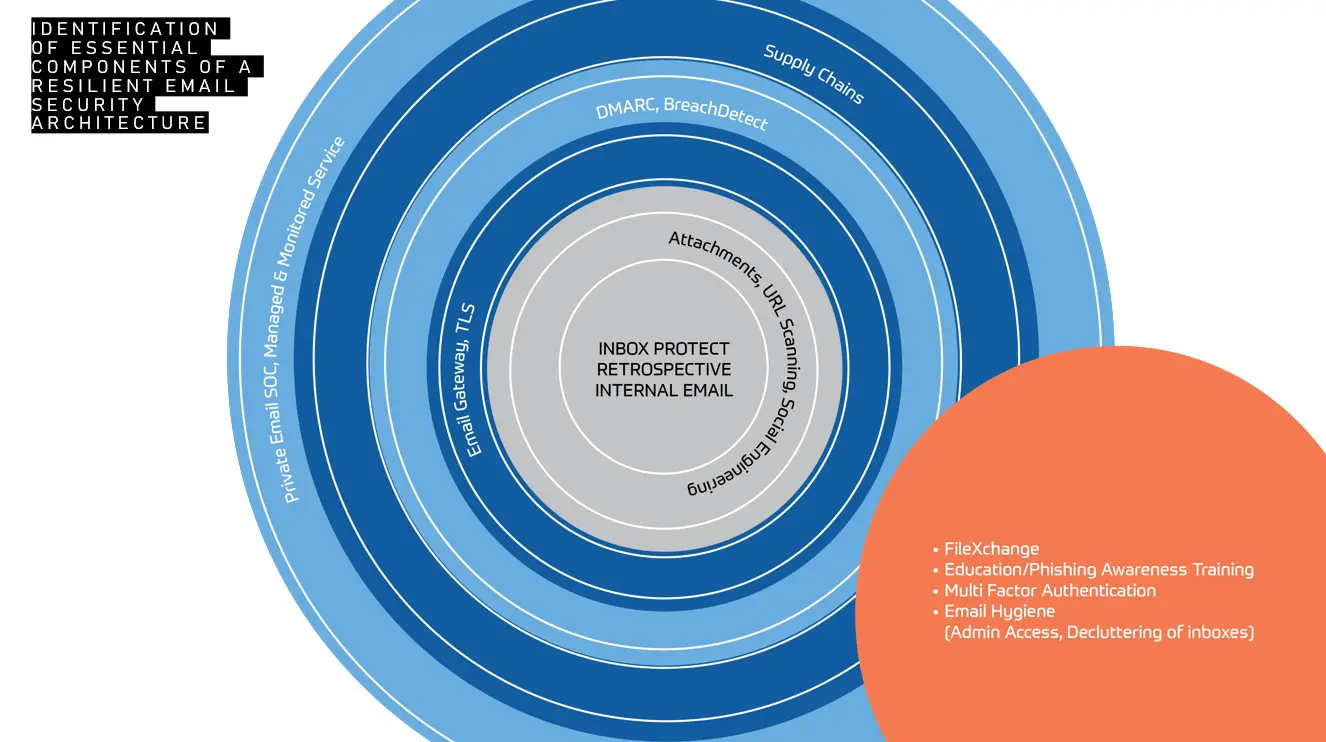
How to Build a Resilient Email Architecture. Strategies for Enhanced Cybersecurity Get a Quote Download Datasheet Email Security > How to Build a Resilient Email Architecture. By Cian Fitzpatrick | 1st May 2024 Email (and email security) is the cornerstone of modern business. Efficient, convenient, productive, it’s the most prolific business tool on which we’ve come to rely. Hence, email remains the primary medium by which cyber threats enter an organisation (91% of threats come through this gateway). Tactics to slide through security systems are becoming increasingly sophisticated, and reliance on human fallibility is key to successful breaches. Effective cybercriminals use a multipronged approach in their endeavours: technology… and social engineering. If we wish to counteract their techniques, we need to proactively defend our assets. And also use a multidimensional strategy. Technology alone is not enough. But it helps. Employee education alone is not enough. But it helps. What are the biggest threats to email security? Bad actors are getting smarter. We’re seeing more malicious QR codes within emails and email attachments. They often appear harmless at first, but post-delivery, they’re able to change destination or characteristic. Likewise with URLs, threats can be triggered and clicks redirected, hours or even days after arrival in an inbox. This can make it difficult for gateway security systems to nab threats as they enter a domain. There’s also been a rise in OneDrive as a delivery method of malicious threats, with files that look initially like they contain nothing untoward. Again, threats are triggered some time later. Whaling and spear phishing attacks are on the increase, where senior staff is tracked and targeted. Information is accumulated from across the web, using social media, and professional platforms to find out who’s-who and where they are. Impersonation techniques involve the clever use of AI and other easily available technology. Remember that this is an industry the size of a country’s economy (third after the US and China, in fact). Compromises in the supply chain are also growing. The use of contractors can be risky. But who doesn’t use contractors and partners? If a supplier’s security is not up to scratch, the knock-on can be huge, and cybercriminals are exploiting smaller suppliers to funnel into larger organisations. Partners are often trusted and the relationship is solid, and so systems don’t flag them up. Human behaviour will always be a stumbling block for organisations. And not just users who are prone to social engineering – which is all of us – there’s also the risk that protocols like DKIM/DMARC are not set up correctly. Compliance regulations and cyber insurance policies may demand these protocols, but correct set-up takes effort and understanding. IT departments are under huge pressure, it’s not surprising then that these protocols become a mere box-ticking exercise. IT staff are often at the point of burn-out and their familiarity with risks, or incessant flags on the systems they monitor, can hinder them from seeing the wood for the trees. What can we do? Central to protecting a cyber environment is a proactive approach. Constant staff-awareness training should be one arm of defence, and technology, the other. A proactive approach means tackling emails before they reach inboxes, before they’re in transit on an organisation’s infrastructure. Once a threat is in an inbox, it could be too late. The onus is then on the user to determine that the email is fraudulent, and this could be the weak link. The sophistication of these scams lies in their appearing sound of character, links and attachments are unthreatening. But they’re manipulable once they’ve reached their destination, and that when they attack. Scammers are taking less of a birdshot approach now. They’re targeting specific people or roles in an organisation, and starting a process of engagement which begins innocently enough. Like this, their emails seem legitimate and go unflagged. Once they have you on a trusting journey, they’re able to lead you to malicious content. DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication protocol. Its aim is to protect an email domain from unauthorised use, particularly email spoofing, or the creation of forged email addresses. Set up DMARC Protection correctly in order to protect businesses from email-based compromises, phishing scams, and other cyber threat activities. Ensure your email security solution scans malicious qr codes Get A Quote The path of an email in an ideal environment On entry to an organisation, an email encounters an antivirus scanner, where it will be reviewed for legitimacy. DMARC and DKIM protocols will be correctly configured and vulnerabilities are constantly monitored on the Dark Web. The AV scanner will look at whether an email’s credentials have been previously encountered, if there’s an existing fingerprint for it, whether or not it has an attachment, link, or QR code. There are three options at this point. The email may be found to be legitimate and risk-free, it may be deemed malicious and blocked, or it may go into a sandbox for further investigation. There are several sandbox environments, one for attachments, one for URLs, one for QR codes. What’s a sandbox? An email sandbox is an isolated environment identical to the user environment. It’s like a laboratory, where an attachment can be exploded or code can be executed in the vacuum of the sandbox without affecting or bringing down the entire network. Sandboxes are particularly effective against Advanced Persistent Threats (APTs), which are custom-developed, targeted attacks. Their aim is to steal data and they’re designed to elude traditional detection methods. Human intervention and observation allows for further research into an attempted attack and action taken. The knowledge and experience of people cannot be underestimated in cybersecurity. Architecture aside… You can have all the best systems in place, solid procedures, cutting edge technology, and the most vigilant IT team, but ultimately, the target for cybercriminals is you and me. Every person in an organisation is a possible access point for a scammer. And so it is up to each person to be the
Meet the team: Topsec MD, Niall Mackey

Meet The Team: Niall Mackey Sales Managing Director Send an Email Niall Mackey Commercial Director Our MD is a sports fanatic, plays pickleball at league level and enjoys celebrating the wins in life. We recently sat down with a cup of tea to discover more of what makes Niall tick. What ensued was a great conversation. We trust you will enjoy it too! Q. 1 Can you share key experiences that led to your role at Topsec Cloud Solutions and how they shape your approach? Niall: A story I tell quite frequently is how I landed up in IT because I was avoiding the religious studies class at school. From an optional study point of view there were just two choices – IT or religious studies. I suppose this is the part where we say “and the rest is history”. But all jokes aside, this key experience does speak of one of the foundational aspects to the approach that led me to my role at Topsec Cloud Solutions which is that I followed my curiosity. Then another stroke of luck came my way in my early career in that “I discovered that while I loved the tech I could also communicate well with people.” This led to my tenure being the IT Manager at Bank of America where my team and I developed the first paperless office! In time, I also held roles at Interoute, Nokie Networks and Horse Racing Ireland. In January 2008, I joined Topsec. All these years later, I still find the work we do fascinating to protect our clients’ businesses from cyber threats. I greatly enjoy the people I work with, both our team and our clients, and I make it my personal mission to fight the baddies every day. Q. 2 Can you outline major shifts in email security and their impact on Topsec’s strategies and the industry? Niall: Firstly, the optics for cyber hackers are changing. For too long, the prevailing image was one of a lone wolf teenage hacker in a hoodie drinking a redbull hacking through firewalls. Now, people are waking up to the fact that cybercriminals run massive businesses themselves. You can now purchase “ransomware as a service” just as you can do for software. Then, when I joined Topsec, most organisations had on-prem solutions. Easily 90% of businesses had their entire business based on their premises. Topsec was always flying the flag for cloud-based solutions, before this term even entered the mainstream. Now, I’d say 98% of our clients have cloud-based email security data solutions. The next big shift I witnessed was the emergence of ransomware. Again, it’s now a commonplace term but it was not even a factor when I first moved into email security. Topsec was ahead of the curve on this one because we had identified that links could be weaponised and developed a URL protector. Our URL protector goes up to 10 links down to check for any poisoned links in the “long tail” behind the link a client may be asked to click on. Quite frankly, our URL protector is the best in the business. Q. 3 How do you ensure a human-centric sales approach amidst technical complexities, and can you share examples? Niall: Although the image of cybersecurity is heavily focused on the tech side of things, it’s not difficult to remember that humans are at the absolute centre of what we do. Cyber attacks have really serious implications and those are borne by the people in the organisation. Especially by those in leadership positions. One of Topsec’s chief differentiators is that we actually have highly trained experts monitoring all of clients’ businesses. Yes, we make extensive use of AI capabilities, and we see technology as an integral part of the “cybersecurity solution stack” for all businesses, but you cannot replace human expertise. We tell our clients our team will know you have a problem before you do – and we’ll already be on it sorting it out. Time and time again, we’ve been told this is why we’ve won their business by clients. Our human touch is highly valued. Q. 4 Highlight a significant success story during your tenure at Topsec that exceeded expectations. Niall: We work with both small and large companies across many industries. To name just a few, we currently have clients in engineering, intellectual property, food, healthcare, agriculture and forestry among others. Our case studies provide real world examples of the work we do for these clients. And the impact this work has had in protecting our clients from cyber attacks. Q. 5 What emerging trends in email security excite you, and how is Topsec preparing for them? Niall: AI is the big new thing on the block, but all the hype takes away the true game-changer this type of technology truly offers. We’ve had AI, or perhaps, more accurately ML (machine learning) solutions and tools in the email security space for years. What we’re seeing now is those tools and solutions become even more refined as firms build Zero Trust Architecture to really build a moat of protection around their data. We’ve also seen Google and Yahoo get serious about prioritising email security with their rulings on DMARC records. Our marketing on this has taken the angle that email is growing up. It’s an accurate description of how massive email providers are taking steps to thwart cyber attacks via inboxes. And it’s a message that’s cutting through. Q. 6 Share strategies for maintaining work-life balance in a high-pressure sales environment. Niall: This is where the pickleball comes in! I’ve loved sport since I was a child and that love has only strengthened over the years. I played and coached tennis for a number of years, but my latest passion has been pickleball. Topsec sponsors a league and I am part of a team. It’s huge fun! My wife constantly asks me why I’m running around like a deranged lunatic, but what can I say, it’s my preferred way to
Safeguarding Against Quishing: Strategies for Enhanced Cybersecurity
Explore effective strategies to secure your business from QR code phishing attacks, strengthen email security and implement robust cybersecurity measures.
Elevating Email Security Standards with Topsec Inbox Protect
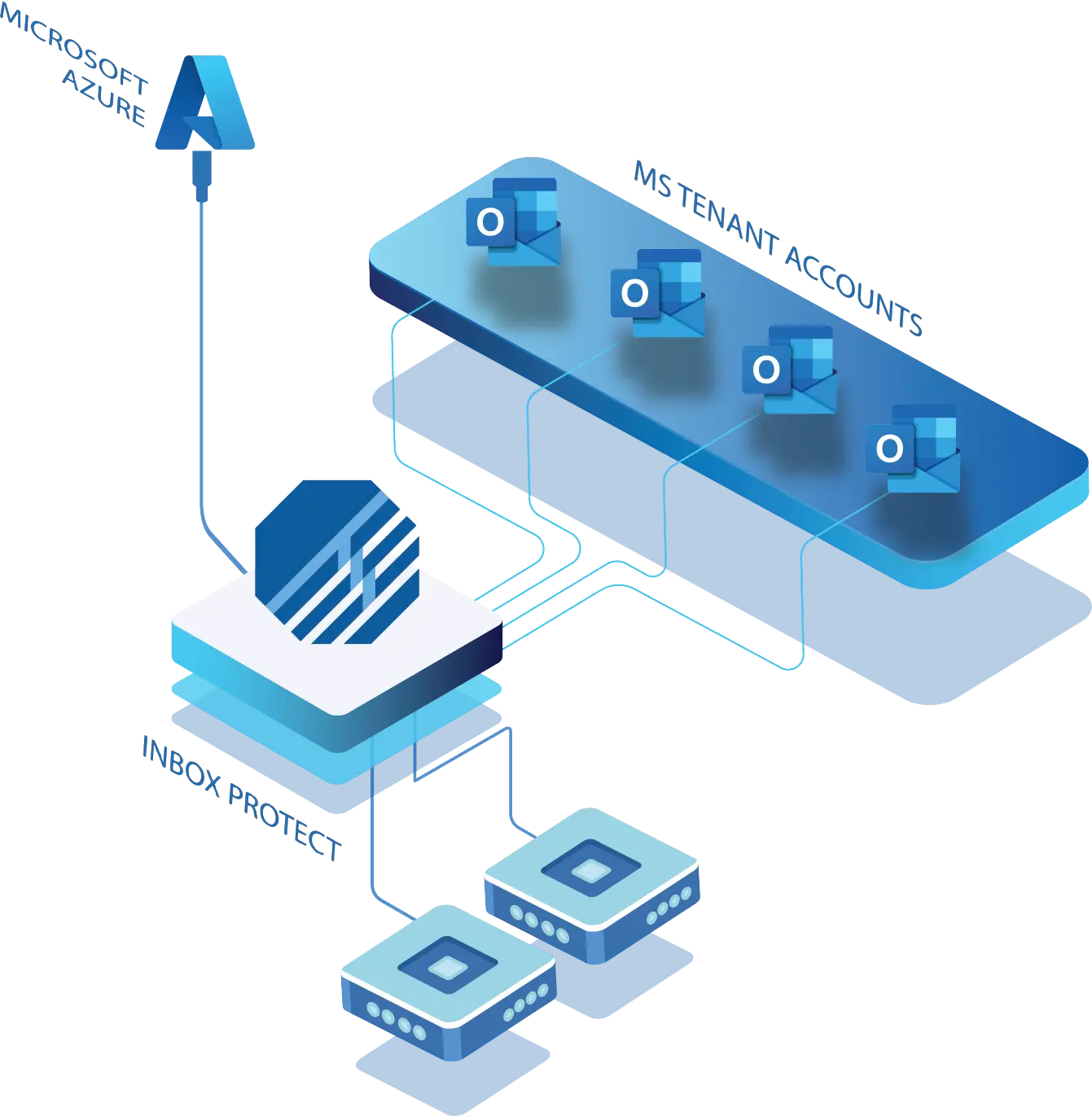
Topsec Inbox Protect:Protect Internal Email Elevate Your Email Security Get a Quote Download Datasheet Email Security > Elevating Email Security Standards with Topsec Inbox Protect By Cian Fitzpatrick | 26th March 2024 In today’s interconnected digital world, email remains the backbone of communication for businesses. It’s email that serves as the conduit for vital information exchange, collaboration and workflow management. However, alongside its undeniable usefulness comes an avalanche of cyber threats that continually test the efficacy of existing security measures. For this reason, organisations need to adopt a zero tolerance approach. And get as tough as nails on anything that even remotely looks like a hack! Platforms like Microsoft Office 365 (O365) provide a layer of email protection, but by no means does this represent enough. The evolving nature of cyber threats necessitates a proactive approach to safeguarding email communications with a multi-layered approach. Enter Topsec Inbox Protect – a comprehensive solution designed to fortify internal mail security and shield organisations from a myriad of potential threats. Inbox Protect and Microsoft 365 Inbox Protect works and is compatible with your Microsoft Tenant. Understanding the Essence of Topsec Inbox Protect At its core, Topsec Inbox Protect represents the toughest defence yet in the realm of email security. By seamlessly integrating with Microsoft users’ mailboxes, it offers an additional layer of protection against malicious entities seeking to exploit vulnerabilities within internal mail systems. Simple and effective, Inbox Protect streamlines the setup process, ensuring that organisations can bolster their email security posture without undue complexity or disruption to daily operations. Mitigating Common Threat Vectors Despite the best efforts of traditional email security measures, certain threats persistently find their way into users’ inboxes, posing significant risks to organisational security and integrity. This shouldn’t come as any great shock when we take into account that 91% of all cyber attacks come through email. Phishing attacks, in particular, continue to plague organisations worldwide, with cybercriminals employing sophisticated tactics to deceive unsuspecting users and extract sensitive information. Don’t forget, cyber criminals are as versed in human psychology as they are in technology. Through advanced scanning algorithms and real-time threat detection capabilities, Topsec Inbox Protect acts as a stalwart guardian, identifying and neutralising phishing attempts before they can inflict harm. But phishing isn’t your only problem. The spectre of malware and ransomware looms large, presenting a clear and present danger to organisations of all sizes. These insidious threats not only jeopardise sensitive data but also disrupt critical business operations, potentially resulting in significant financial losses and reputational damage. With attachment virus scanning and real-time mail monitoring, Inbox Protect stands as a bulwark against such pernicious threats, fortifying organisations’ defences and mitigating the risk of data breaches and system compromise. Is M365 fully protecting you against all email borne attacks? Get A Quote Embracing a Second-Layered Security Approach Cyber threats are both omnipresent and ever-evolving, a holistic approach to email security is paramount. When organisations speak about building a moat, email security has to be included in the strategy if you want to ensure growth and sustainability. Topsec Inbox Protect complements existing security measures by providing a second-layered defence mechanism, thereby augmenting organisations’ resilience to emerging threats. By fortifying both internal and external mail systems, Inbox Protect establishes a comprehensive security perimeter, safeguarding against a broad spectrum of potential attack vectors. The ease of setup and deployment further underscores Inbox Protect’s appeal, enabling organisations to bolster their email security posture with minimal overhead and administrative burden. Furthermore, the ability to retroactively scan historical mail within a 14-day timeframe ensures that organisations remain vigilant against threats from both past and present communications. This enhances overall security efficacy and incident response capabilities. Key Advantages of Topsec Inbox Protect Adding Inbox Protect to your “email security stack” will provide your organisation with a number of benefits: 1. Comprehensive Inbox and Subfolder Protection Ensures thorough scanning and detection of malicious content within primary inboxes and subfolders, thereby minimising the risk of undetected threats. 2.Real-time Internal Mail Scanning: Provides continuous monitoring of internal mail traffic, enabling swift detection and neutralisation of potential threats in real-time. 3. Attachment Virus Scanning: Employs advanced scanning techniques to scrutinise email attachments for malware and ransomware payloads, mitigating the risk of infection and data loss. 4. Spam Content Scanning: Identifies and removes spam and unwanted email content, thereby reducing the likelihood of data exposure and compromising sensitive information. 5. Known Bad Mail Address and Domain Check: Verifies sender addresses and domains against known malicious entities, preventing unauthorised access and fortifying organisational defences. 6. URL Rewriting and Detailed URL Analysis: Proactively rewrites URLs and conducts comprehensive analysis of embedded links, mitigating the risk of users inadvertently accessing malicious websites and falling victim to phishing scams. 7. Sandboxing: Introduces attachment sandboxing to internal email, exploding attachments within a dedicated virtual environment for in-depth analysis. 8. URL Triggering: Tracks all URLs within the tenant and forces deletion of emails that become triggered post delivery. How Topsec Inbox Protect Works Cyber Threats Are Only Increasing It’s no fun to be the harbinger of bad news. But at the same time, pretending a threat doesn’t exist is the fastest way to fall prey to one. Cyber attacks are increasing. Every organisation that wants to safeguard their data assets and maintain operational continuity needs to prioritise email security. Why not test Inbox Protect with a 7 day free trial? Your inbox, reputation and customers will thank you for taking the extra step to protect your inbox. And the cyber criminals will be thwarted before they even start. That’s a win/win in our book! Protect your internal email with topsec inbox protect Contact Us

